Motivations
By learning core malware analysis techniques you are able to
- Asses the nature of malware threats
- Determine the scope of incident
- Extract malicious artifacts
- Fortify system and network defenses
Stages of malware analysis techniques
There are 4 stages
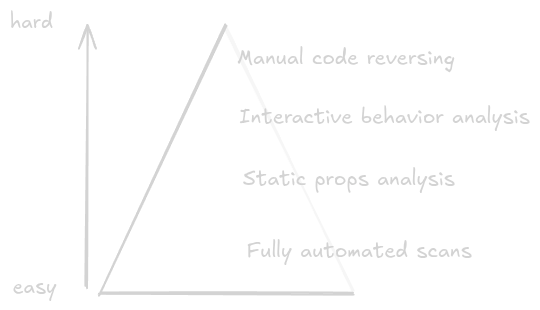
- Fully Automated Analysis
- Using sandbox tools like VirusTotal, Hybrid Analysis
- Fast but limited insight
- Good for triage and scale
- Static Properties Analysis
- Examine file structure, strings, headers, metadata
- No execution required
- Fast, safe, reveals potential capabilities
- Behavioral Analysis
- Execute in controlled environment
- Monitor file system, registry, network activity
- Shows actual runtime behavior
- Code Analysis (Manual Reversing)
- Disassembly and debugging
- Most time-consuming but most comprehensive
- Requires knowledge of assembly, C, memory
- Reveals all capabilities and logic
Dangers of OSINT for Targeted Malware
Critical Risk Uploading targeted malware to public sandboxes can alert the attacker.
- Attackers monitor VirusTotal for their file hashes. Uploading reveals you’ve discovered their operation
- They may adapt their C2 infrastructure and modify malware
- Sharing sensitive samples may violate organization policies or get you in legal trouble
- Samples may contain sensitive victim data